WHAT'S HAPPENING?
What is CVE-2025-53770?
In July 2025, Microsoft confirmed active attacks targeting on-premises SharePoint servers . These attacks exploit multiple vulnerabilities, including the recently disclosed CVE-2025-53770 and CVE-2025-53771 , which can lead to unauthenticated remote code execution (RCE).
This issue does NOT affect SharePoint Online (Microsoft 365) but affects all on-premises versions— SharePoint Server 2016 , SharePoint Server 2019 , and SharePoint Subscription Edition .
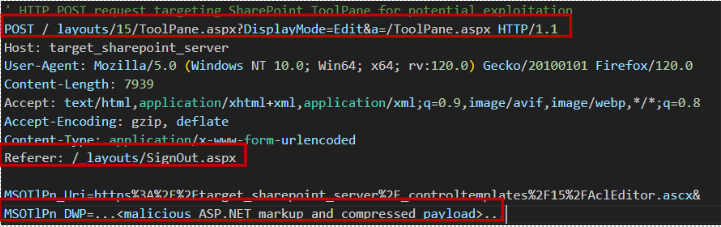
The attack chain often starts with a crafted POST request to
ToolPane.aspx
, as shown below:
POST http://<SharePointServer>/_layouts/15/ToolPane.aspx Content-Type: application/x-www-form-urlencoded Content-Length: 3578
Once inside, hackers drop malicious files (like spinstall0.aspx) and gain persistence. They may even disable antivirus, steal credentials using tools like Mimikatz, and spread ransomware across the network.
Why this exploit is serious.
Hackers can take over unpatched SharePoint servers without login credentials.
Exploits are already being used by Chinese state-linked groups such as Linen Typhoon , Volt Typhoon , and Storm-2603 .
Storm-2603 has been deploying ransomware (Warlock) in compromised environments, often after weeks of lurking in the system.
Who is at risk?
Organizations running on-premises SharePoint that is exposed to the internet.
Those using cracked or outdated versions of SharePoint—you won’t get Microsoft’s security updates, and cracked builds may already be compromised.
Businesses with weak endpoint protection or no active monitoring.
How hackers will typically operate
ToolPane.aspx via CVE-2025-53770.\> whoami to learn user privileges.services.exe and registry tweaks to turn off Defender.spinstall0.aspx, spinstall1.aspx) and scheduled tasks.
What IT Admins Should Do Immediately
The CVE-2025-53770 exploit proves how quickly hackers weaponize new vulnerabilities. If you run SharePoint on-premises, patching is non-negotiable. Assume attackers may already have a foothold if you’re unpatched—conduct forensic checks and close any gaps now.
Instructions
Enable AMSI & Defender
-
Turn on Antimalware Scan Interface (AMSI) in Full Mode.
Learn how to enable AMSI Full Mode -
Ensure Microsoft Defender Antivirus or an equivalent EDR is active.
Microsoft Defender Antivirus documentation
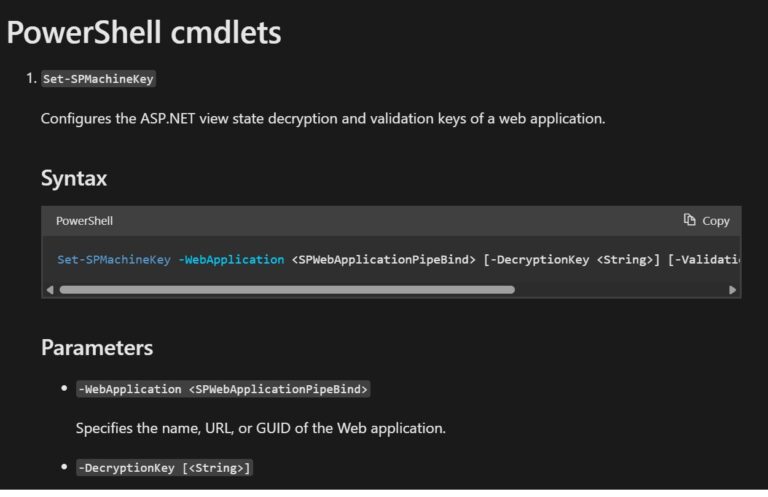
Rotate ASP.NET Machine Keys
-
Rotate ASP.NET Machine Keys:
Run
Set-SPMachineKeyvia PowerShell, or go to Central Administration → Monitoring → Machine Key Rotation Job and select Run Now. -
Restart IIS:
Execute
iisreseton all SharePoint servers to finalize changes.
Audit for Compromise
- Look for suspicious
.aspxfiles (e.g.,spinstall0.aspx). - Check IIS logs for ToolPane.aspx POST requests.
- Scan for scheduled tasks, abnormal registry edits, or new services.

Isolate & Monitor
- If you suspect compromise, take the server offline to avoid ransomware spread.
- Use Microsoft Defender for Endpoint or equivalent to hunt for IOCs.
Tips for regular users
Don’t ignore system updates. Your IT team relies on patching to protect company data.
Report suspicious behavior (sluggish servers, odd files) early.
Avoid cracked enterprise software. These versions are time bombs—they’re often pre-infected and never get security patches.